Are you ready for the NIS2 Directive?

Get ready in time, ensure NIS2 compliance and strengthen your cyber resilience.
The NIS2 Directive is the European Union's response to the growing number of cyber threats: The new “Network and Information Security Directive” introduces stricter cybersecurity regulations for more sectors and companies. The objective remains the same: to protect (critical) infrastructures and increase resilience to cyberattacks.
As an EU directive, this set of rules must be transposed into national law by the member states. In Germany, the NIS-2 Implementation and Cybersecurity Strengthening Act (NIS2UmsuCG) has been drafted for this purpose. However, due to new elections in early 2025 and the principle of discontinuity (of bills), its entry into force was postponed until the current legislative period and was published and into force on December 6th 2025. Nevertheless, national laws have already come into force in more than seven EU member states before, including Belgium, Italy, Croatia and Hungary.
German companies were therefore well advised to use the time they have gained to address the requirements of the NIS-2 Directive. Failure to comply with the minimum measures could result in fines of up to €10 million or 2% of annual global turnover. In addition, NIS-2 postulates a higher standard of management liability, including liability with private assets.
Prepare and implement the NIS-2 requirements with our expertise: We can assess your current situation, draw up a roadmap and help you become a compliant information and cyber security organisation.
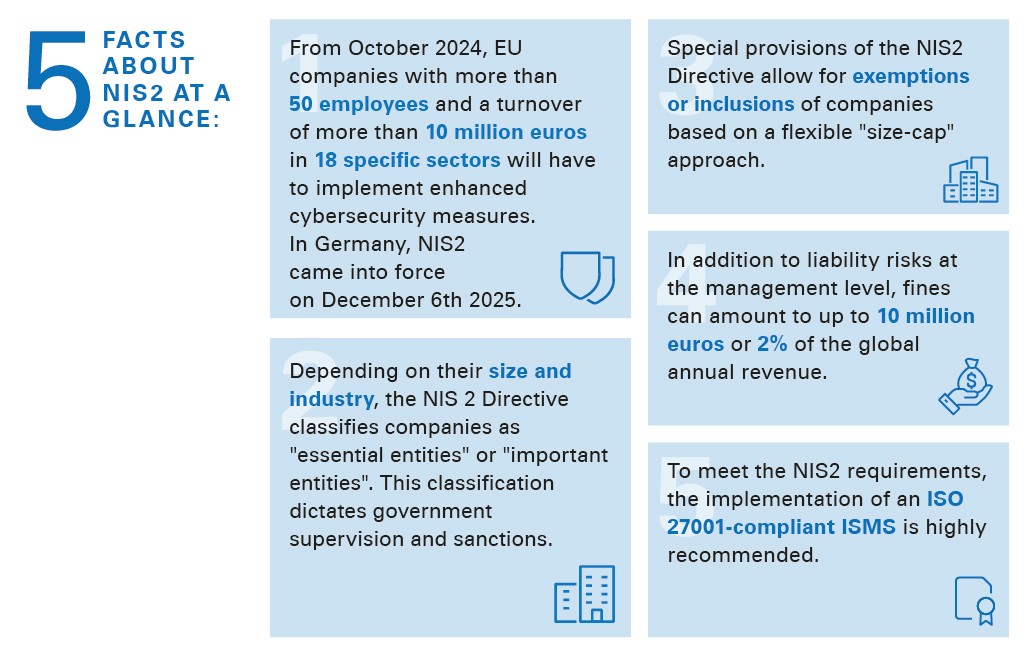
Am I affected by the NIS2 Directive?
The NIS2 Directive makes cybersecurity relevant for many more companies: Experts estimate that approximately 150,000 companies across the EU are affected. This is because NIS2 also applies to smaller companies with 50 or more employees or an annual revenue and balance sheet total of 10 million euros. In addition, the number of sectors affected has been increased from eleven to 18. Eleven sectors are considered highly critical (essential entities) and seven more are otherwise critical (important entities). To determine the extent of the impact (relevance analysis), all business units and associated companies must be considered and evaluated on the basis of the Group's allocation rules and statutes.
What is the difference between essential and important entities?
The classification is based on the size of the company and on the sector: Essential entities are organizations that operate in a critical sector and have more than 250 employees or an annual revenue of more than 50 million euros and a balance sheet total of 43 million euros.
Essential critical sectors:
- Energy: Electricity, oil, natural gas, hydrogen, district heating and district cooling
- Transport: Aviation, rail transport, shipping, road transport
- Banking
- Financial market infrastructure
- Healthcare: Hospitals, research, pharmaceuticals, medical devices
- Drinking water supply
- Waste water treatment
- Digital infrastructure: Data centers, DNS services, cloud computing
- ICT service providers: Managed service and managed security service providers
- Public administration: Public authorities and offices at the national and regional level
- Outer space: Operators of ground infrastructure
All other organizations with more than 50 employees or an annual revenue of more than 10 million euros are considered important entities.
Important critical sectors:
- Postal and courier services: Letter and parcel delivery
- Waste management: Waste collection and recycling
- Chemicals: Production and trade of chemical substances
- Food: Production, processing, and distribution of food
- Production: Manufacturers of medical devices, machinery, vehicles, and electrical appliances
- Digital services: Search engines, marketplaces, social networks
- Research: Research institutions
Important: EU member states can expand the requirements if a company meets certain criteria that indicate it plays a key role for society, the economy or for certain sectors or types of services.
What will be changing under NIS2?
The most significant change is the expanded scope of companies required to comply. Additionally, the cybersecurity requirements are now more stringent: affected companies must implement appropriate “state of the art” measures in areas such as risk management, business continuity management (BCM), supply chain security and incident response.
In addition, national regulatory authorities now have stronger enforcement powers, with stricter penalties for violations as well as more rigorous reporting obligations. Companies will now required to report security incidents promptly — no later than ‘24 hours’ after becoming aware of them by submitting an initial early warning report and following up within 72 hours by submitting an updated detailed report.
What are the penalties and liability risks?
Not only are the requirements becoming more stringent, but the pressure to enforce them is also increasing – such as through tighter sanctions and personal liability at the management level. Non-compliance with the NIS2 Directive could result in:
- Fines of up to 10 million euros or 2% of the total global annual revenue for essential entities
- Fines of up to 7 million euros or 1.4% of the total global annual revenue for important entities
- Management liability for violations of the Directive
- Management can be held liable with their personal assets.
- Ban/discharge from managerial functions
- Temporary suspension of services
What NIS2 requirements do I have to meet?
In order to be NIS2 compliant, a security program must cover the following requirements at a minimum:
Establishing NIS2 Readiness through ISMS implementation
An Information Security Management System (ISMS) to ISO/IEC 27001 provides a solid foundation for meeting the specific requirements of NIS-2. It can be implemented in part or in full and can even be independently certified.
The ISMS helps you to identify and assess risks, take appropriate security precautions, and monitor their effectiveness. It also promotes a proactive approach to information security through regular reviews, audits, and continuous improvement.
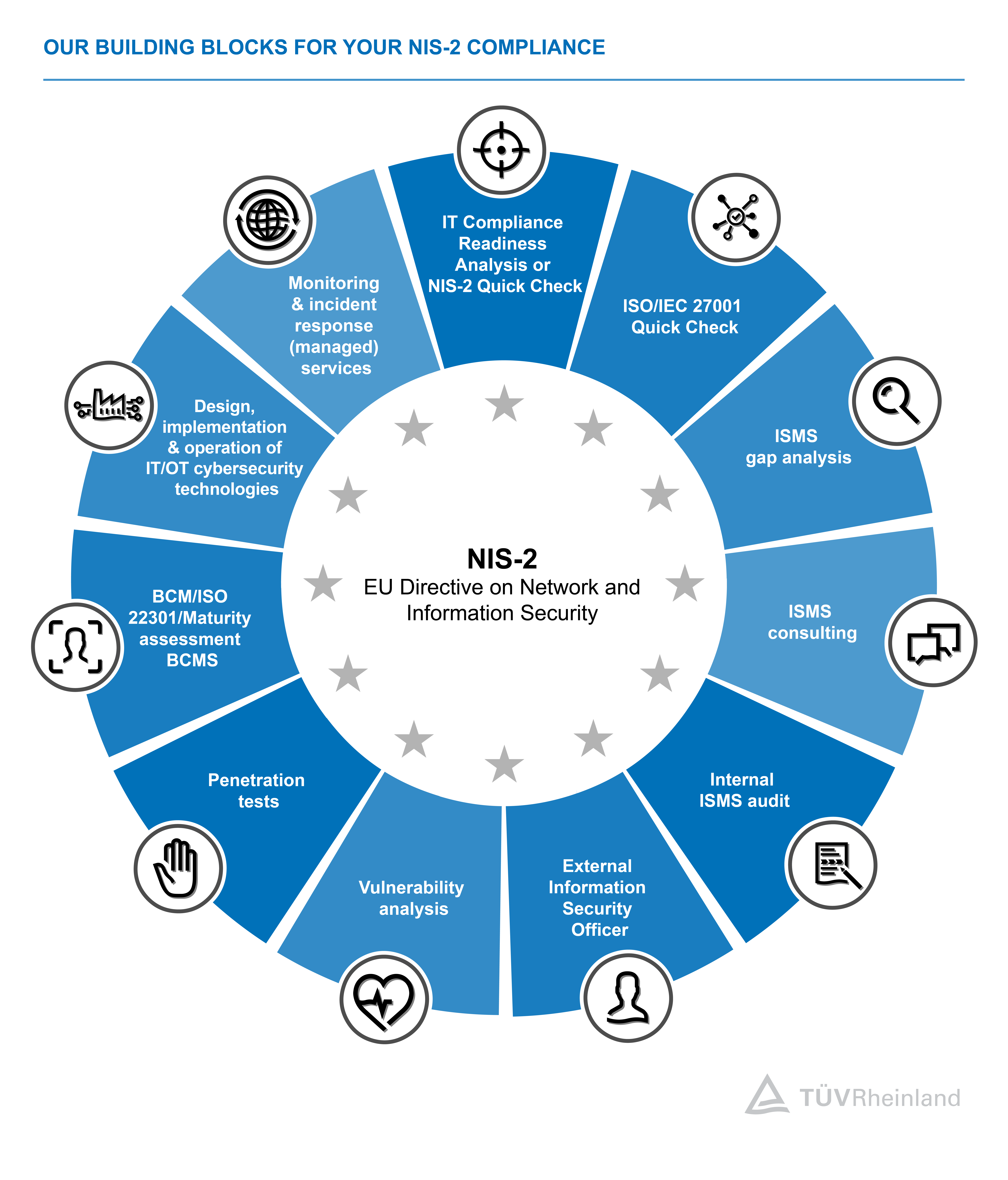
How TÜV Rheinland can support you with NIS2:

NIS2 Quick Check
Check IT Compliance Readiness Assessment NIS-2 or NIS-2 QuickCheck Find out if and how the NIS-2 Directive affects your organisation. As part of our IT Compliance Readiness Assessment, we also identify and prioritise company-specific risks and areas for action, and analyse the extent to which the existing system is able to meet further (future) requirements, such as the EU Data Act, Cyber Resilience Act, DORA (for the financial sector), etc. A comprehensive report with an action plan completes the project and forms the basis for setting up an IT compliance management system, with or without an ISO 27001 ISMS, depending on the client's requirements. If you are looking for a short and concise introduction to the subject, we recommend our NIS-2 QuickCheck. In this process, we check whether and in which areas NIS-2 is relevant to your organisation (relevance analysis).

Comprehensive consulting services
Use our consultancy services to comply with the NIS-2 Directive and national implementing legislation, whether in Germany or in other EU member states. These services range from detailed NIS-2, BCM, ISMS, data protection and compliance gap analysis to maturity assessments and security solution design. We also test and evaluate your security technologies to prevent, detect and respond to attacks.

Implementation and operation
With the final report of the NIS-2 IT Compliance Readiness Assessment, you will receive an action and remediation plan that you can either implement with your own resources or, again, rely on the expertise of TÜV Rheinland. We will work with you to implement the measures based on our many years of implementation experience and best practices. We also offer complementary tool-based implementation services: you can purchase your own solution or get it as a managed service with variable modules - from service implementation and basic support to full operation, including SOC (Security Operations Centre) services.
Your benefits at a glance:
- Comply with legal requirements
- Protect critical business processes
- Stay on top of IT risks
- Introduce targeted security measures
- Invest in the right measures
- Minimize personal liability risks
- Maximize information security
Let us support you towards NIS2 compliance.
If you are unsure whether your business is affected, we are here to help provide clarity by conducting a Relevance Analysis.
We can support you with comprehensive consulting, customized service modules and reliable implementation to get you to your goal.
Contact

/tuv-rheinland-business-continuity-management-bcm_core_4_3.jpg)



-cybersecurity-services-1_core_4_3.jpg)
