ISO/IEC 27001 Certification – Systematically Managing Information Security

Amendment 1: Changes of ISO standards regarding Climate Change
| Amendment 1 | 504 KB | Download |
Protect Your Business Data with ISO 27001 Certification
Complex IT systems are now capable of processing a wealth of information quickly. To ensure safe processing, information must be confidential and available, and its integrity must be maintained. After all, if information starts to leak out, it can become a trust problem and lead to a competitive disadvantage.
Particularly in the age of social media and ransomware, information security is becoming increasingly important, but, at the same time, ever more vulnerable to threats. It therefore follows that well-organized and demonstrably operational professional IT security management is a pressing requirement for companies.
What is ISO/IEC 27001?
ISO/IEC 27001 is the internationally recognized standard for Information Security Management Systems (ISMS). It provides a systematic approach for planning, implementing, monitoring, and continually improving information security within organisations, covering not only IT processes but also organisational aspects like personnel and infrastructure.
ISO/IEC 27001:2022 – Transition by Autumn 2025
The transition period to the new standard version runs until autumn 2025. Organisations already certified to ISO/IEC 27001 can integrate the transition audit into their regular audit process early. Secure your ISO/IEC 27001:2022 certification promptly – our experts are glad to assist you.
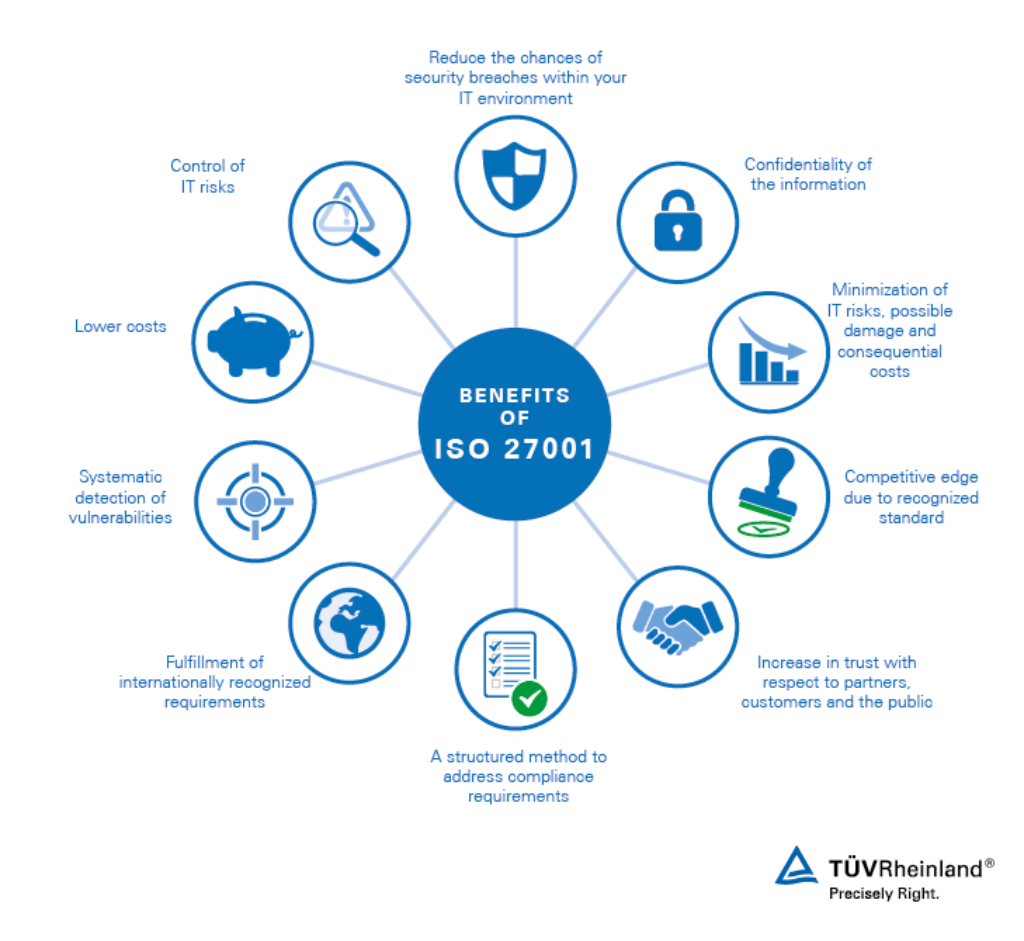
Benefits of ISO/IEC 27001 Certification
- Sustainable protection of sensitive data: efficiently safeguard your information, data, and business processes from cyber threats and theft.
- Independent trust and compliance proof: reinforce stakeholder confidence with objective certification of your ISMS.
- Continuous improvement: boost your IT systems’ availability and implement effective control and governance mechanisms.
- Employee awareness: enhance staff awareness of information security and data protection.
- Security gap identification: systematically uncover and mitigate potential vulnerabilities.
- International recognition: meet globally accepted information security criteria and differentiate from competitors.
- Cost reduction: avoid inefficiencies and security incidents, leading to lower costs.
- Insurance premium reduction: certification can have a beneficial impact on your insurance terms.
The New ISO/IEC 27001:2022
Published in October 2022, the updated ISO/IEC 27001:2022 standard addresses increasing information security challenges. Key changes include:
- Alignment with the Harmonized Structure (HS), facilitating integration with other management system standards.
- A greater focus on processes and their interactions.
- A revised Annex A: the number of controls has been reduced from 114 to 93 and restructured into four categories.
- Increased emphasis on cybersecurity and data privacy, highlighting current threats and technologies.
Additionally, the transition deadline is 31 October 2025. Organisations must complete the upgrade by then to maintain certification validity.
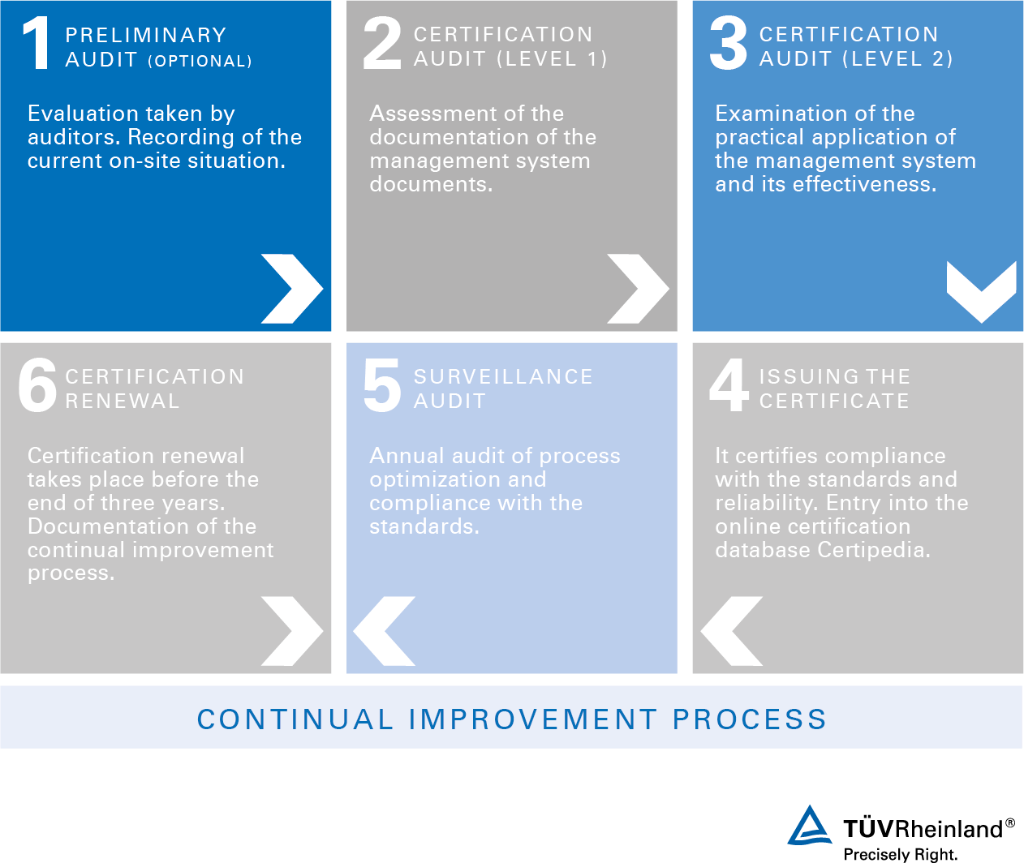
ISO/IEC 27001 Certification Process
The certification process follows a structured approach to ensure your ISMS meets international requirements—from initial assessment to certification audit and ongoing surveillance audits—for sustainable information security and continuous improvement.
Most asked questions in regard to ISO 27001 certification
Learn More About Information Security Management
| Flyer – Information security management system | 188 KB | Download |
Disclaimer: At TÜV Rheinland, the neutrality, objectivity, independency and impartiality of our activities are of utmost importance. Our assessment and audit activities follow these values in compliance with the applicable accreditation requirements. All the necessary structural, organizational and processual measures are in place in all levels of the organization in order to avoid conflicts of interest (e.g. rigorous separation of consultancy and certification) and to ensure impartiality. We do not offer or provide management system consultancy by an accredited certification body for management systems. Within the TR Group, we ensure a minimum 2-year interval between management system consultancy and certification activity for the same costumer.
Contact






