Penetration Tests

Detect security vulnerabilities in time and protect valuable data.
The advancing digitalization is noticeable in every industry and in every company size. Whether in the chemical and pharmaceutical industry, automotive industry, finance and insurance industry or in small and medium-sized enterprises (SMEs), the changes are the same: processes are digitized and systems are interconnected, critical business applications are increasingly web and/or mobile-based and more and more applications and data are being moved to the cloud.
This opens up new attack options for cybercriminals.This development is also confirmed by the results of our Cybersecurity Trends 2024 , which show that cyberattacks are increasingly threatening the existence of companies and that attacks are becoming more and more professional. The growing importance of cyber resilience is also reflected in the constantly increasing regulation in this area, some of which even require penetration tests to be carried out.
The digital transformation requires new thinking on the part of corporate management and IT managers in terms of cybersecurity and data protection measure since cyberattacks represent a challenge in everyday business that should not be underestimated.
Penetration Tests by TÜV Rheinland – Your benefits
✔ Identify vulnerabilities early – We detect security gaps before attackers can exploit them.
✔ Ensure compliance – Meet all relevant security standards and strengthen the trust of your customers and partners.
✔ Certified experts – Our testers are highly qualified and hold recognized certifications such as OSCP.
✔ State-of-the-art attack scenarios – Our experts stay up to date with the latest threats through continuous training.
✔ Technical specialization – Each tester focuses on a specific area to ensure maximum expertise.
✔ Efficient project management – Clear processes, structured reports, and professional management ensure smooth testing.
✔ Realistic attack simulation– Our Red Team campaigns demonstrate your organisation's resilience to modern, targeted cyber attacks and provide practical suggestions for improving your detection and response capabilities.
✔ TÜV Rheinland stands for quality and expertise – As an experienced and independent testing body, we offer penetration tests that meet the highest standards.
Therefore, identify potential vulnerabilities in your IT infrastructure by means of a penetration test, check the effectiveness of existing protective measures and find out where systems do not meet the security requirements.
Get an objective assessment of your IT security and discover your vulnerabilities before hackers find them.
Different variants of a penetration test
Various methods can be used to identify vulnerabilities. Which option is the right one for your company depends on your existing IT infrastructure In a personal conversation, we determine your needs and analyze the existing systems to find the right penetration test method for you. Take a look at our pentesting portfolio.
Companies are increasingly deploying Large Language Models (LLMs) in chatbots, assistant systems, or automated decision-making processes. However, these powerful AI models pose significant security risks – ranging from uncontrolled data leaks to manipulation through targeted attacks. With our specialized LLM penetration testing, we identify vulnerabilities and help you secure your AI models reliably.
What vulnerabilities do we test for?
Our tests are based on the OWASP LLM Top 10 and cover, among others, the following risks:
- Prompt Injection: Manipulating input prompts to alter the model’s behavior or extract confidential information.
- Data Leaks: Unintentional disclosure of sensitive data from the training process or during use.
- Model Theft: Unauthorized access to the model to replicate it or use it for malicious purposes.
- Training Data Poisoning: Insertion of manipulated training data to influence model outputs.
- Misuse and Security Gaps: Exploiting LLMs for disinformation, spam, or social engineering, as well as insecure API usage.
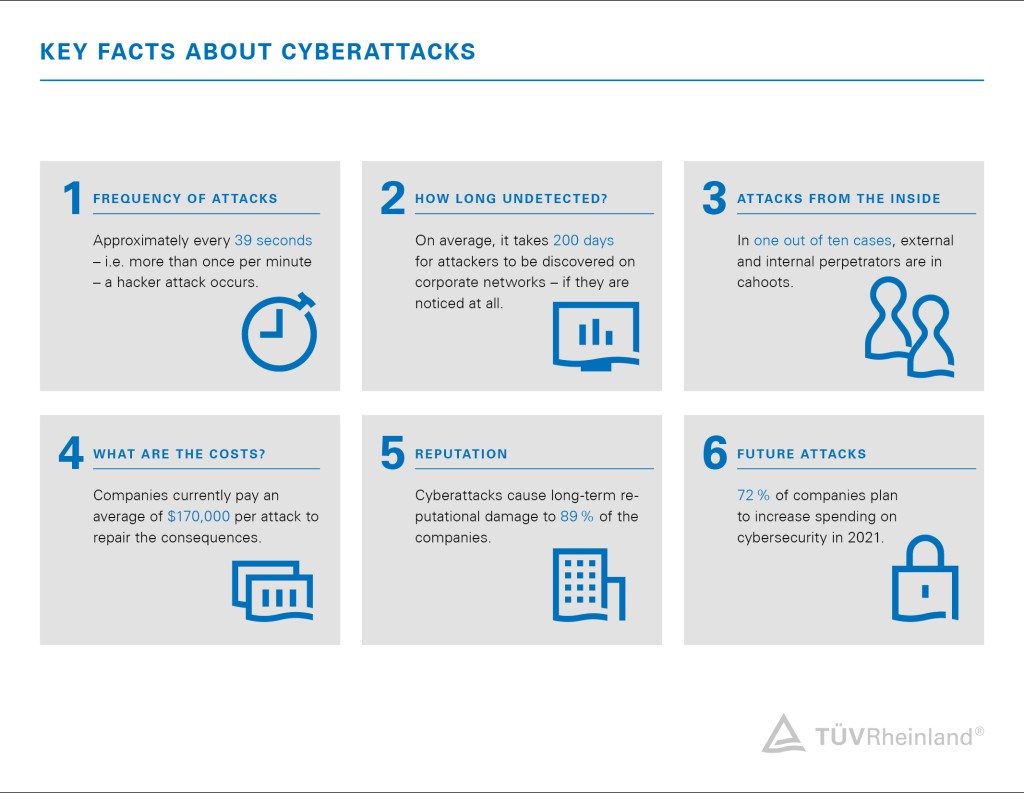
The external penetration test symbolizes the "classic" cyber attack from the outside. Here, our IT security expert attempts to penetrate the company's internal network via the systems accessible from the Internet. The focus of the investigation is on the firewall and systems of the Demilitarized Zone (DMZ - a network that acts as a buffer zone and is monitored by the firewall, such as web or mail servers) in order to subsequently uncover the possibilities of data access or theft. Our experts also try - if allowed - to penetrate the internal network from the DMZ.
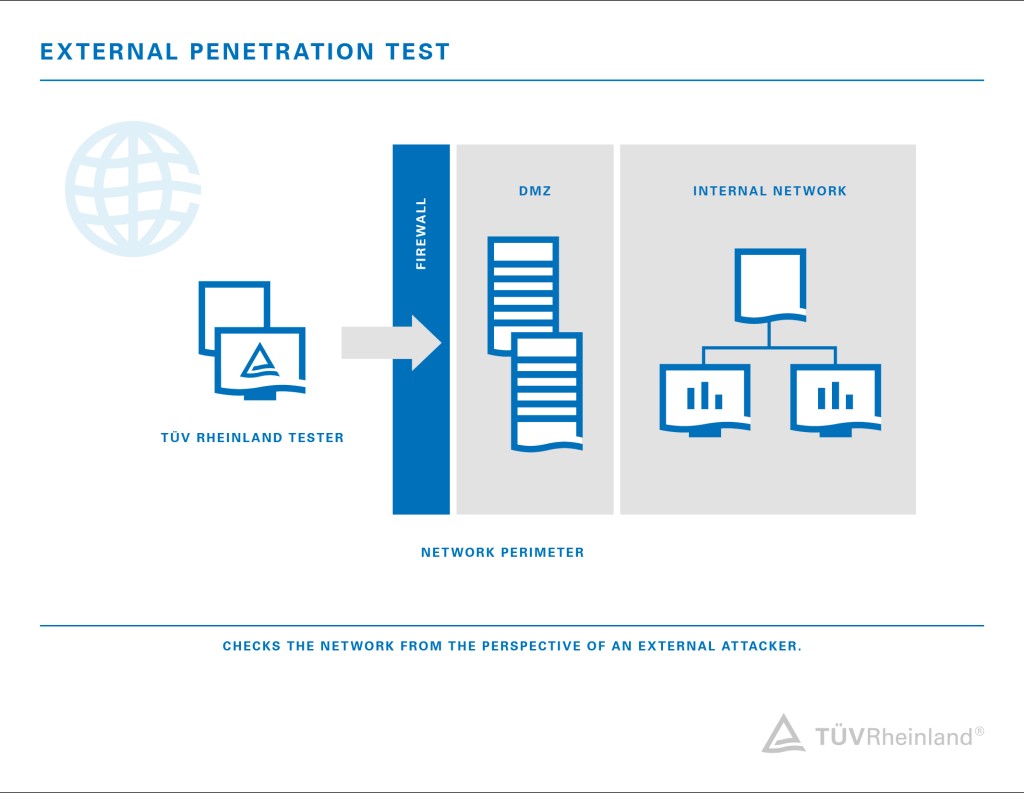
In an internal penetration test, the starting point is within the corporate network, i.e. the attacker has already gained access to the internal network. This simulates the case where an attacker is already on an employee's device. Thus, the goal of the internal pentest is to determine what damage can occur if corporate access is criminally misused. An attack from within the company can often cause more damage in less time than an external attack, as some protection systems have already been bypassed or overcome.
In this method, our experts simulate a cyber attack using the tactics, techniques, and procedures of real attackers. We determine the focus and objectives of the Red Team campaign together with you in advance. If required, we work with you to identify the most critical attack vectors - in relation to your cyber resilience - before moving on to an attack simulation.
Compared to a penetration test, the goal of a Red Team campaign is not to uncover as many vulnerabilities as possible, but to achieve the defined campaign objective with a targeted exploitation of relevant vulnerabilities. The results provide you with information about the resilience of your company or division with regard to cyber attacks. In addition, the results help your own experts to optimize internal monitoring systems and processes within the company in order to detect attacks earlier. This minimizes the risk of major damage to your company.
Further information about the Adversary Simulation can be found here in our information flyer.
During the IoT penetration test, our experts check your IoT ecosystem from a hacker's perspective and detect vulnerabilities and security issues. For comprehensive protection, we test the entire IoT ecosystem – all connected services and applications. If required, we can also examine individual components and support you with the following individual services:
- Security analysis of the IoT devices
- Security analysis of a medical device
- Security analysis of automotive components
- Security analysis of mobile applications
- Security analysis of the backend
- Security assessment of the backend
Read detailed information about IoT penetration testing in our related flyer. Learn more.
Software can conclude programming errors, security gaps or functions, which can be abused for cyberattacks. The source code audit analysis is capable of detecting those potential safety risking weak points in the functionality and structure of the application.
Already during the development phase we highly recommend our audit as quality assurance measure.
For this purpose, our specialists need access to the entire source code or selected modules, which are analyzed by us from a development perspective using automated tools and manual means.
You receive a detailed report, documenting weak points and identifying suitable measures for targeted remediation.
Request a quote now.
The web application testing is a penetration test based on the Open Web Application Security Project (OWASP) Testing Guide. The identification of the OWASP Top 10 vulnerabilities are the focus of the investigation. However, our experts also look for less common application-specific vulnerabilities in order to achieve the best possible level of protection for your web application. Afterwards, we summarize the results of the analysis as well as recommendations for remedying the vulnerabilities in a report.
You can find more information in our flyer Security for your web application.
The hack box enables our experts to perform penetration tests remotely. The remote solution is particularly advantageous when the presence of our colleagues is challenging for various reasons (for example home office workplaces, or large geographical distances). The hack box is a specially configured and protected computer that is delivered by mail. The installation of the hack box into the internal network is designed for simplicity and does not require any special prior knowledge, which makes the collaboration between us and the users easy.
You can find out all the details about the process and handling of the hack box here.

Red Team Campaign (Adversary Simulation)
In this campaign, our experts will simulate a targeted cyber-attack on your company, using the same tactics, techniques and procedures as real attackers. Unlike traditional penetration tests, the focus is not on identifying vulnerabilities across the board, but on successfully exploiting critical attack vectors to achieve defined campaign goals.
The aim is to realistically test your organisation's cyber resilience, identify specific weaknesses in your processes, technology and response, and provide valuable insights to improve your IT security. We define the focus, objectives and attack vectors in close consultation with you in advance, e.g. gaining access to sensitive data, circumventing security mechanisms or intruding into systems undetected.
The results show how resilient your company is against modern attacks and provide targeted recommendations for optimising your monitoring, detection and response processes. Red team campaigns therefore help to identify risks at an early stage and prevent damage effectively. You will find details of our services that can be used as part of a red team campaign below, or booked independently.
As part of a Red Team Campaign, we typically assist companies in identifying critical attack vectors based on their specific threat landscape. First, we work with you to define the campaign's goals, scope and rules. Our red team then carries out simulations of advanced attacks, such as those carried out by cybercriminals, without alerting the IT security department in advance. This reveals vulnerabilities in monitoring systems and detection mechanisms. Our detailed final report highlights the attack vectors used and provides specific recommendations for optimizing your security measures and staying one step ahead of cybercriminals.
Threat-Led Penetration Testing (TLPT) is a structured form of attack simulation and a development of traditional red team methods in IT and information security. Since the EU-wide Digital Operational Resilience Act (DORA) came into force, TLPT has become mandatory for many financial institutions.
Our experts will guide you through every phase of the TLPT process, from planning and defining objectives (scoping), to realistic implementation and evaluation, and finally deriving concrete measures to strengthen your cyber resilience.
We simulate targeted intrusion attempts to test the effectiveness of your physical security measures. Our aim is to access security-critical areas such as offices, server rooms and archives, or even infiltrate the internal network, without being noticed — just as real attackers would try to do.
In advance, our experts gather specific information from publicly available sources (OSINT), through on-site observations or telephone research. Based on this information, we analyze potential vulnerabilities in buildings, access controls, and organizational processes. Working together with an internal contact person, we coordinate the procedure and develop realistic access scenarios, which are then tested in practice.
The outcome is that you receive a comprehensive evaluation of whether your access regulations, security processes, and employee behavior can withstand a realistic attack. At the same time, we raise awareness of potential risks among your teams and provide concrete recommendations for optimizing your physical security measures.
Targeted phishing campaigns are an effective way of raising your employees' security awareness. Our simulated attacks use realistic scenarios tailored to your company, based on current attack methods and your internal structure. We test your employees' behaviour using specially prepared phishing emails, fake websites and scenario-based/customised malware simulations, and redirect them to TÜV training pages if they click on a link.
We work with your internal contacts to develop realistic attack scenarios, present them, and carry out the campaign flexibly over several days or weeks. Our aim is to identify specific gaps in the actions of individual employees or entire departments, providing decision-makers with a sound basis for further measures.
The result is a detailed report containing clear figures and graphics, as well as a thorough evaluation of user behaviour. This enables targeted and effective training measures to be designed.
Detect security vulnerabilities thanks to pentests
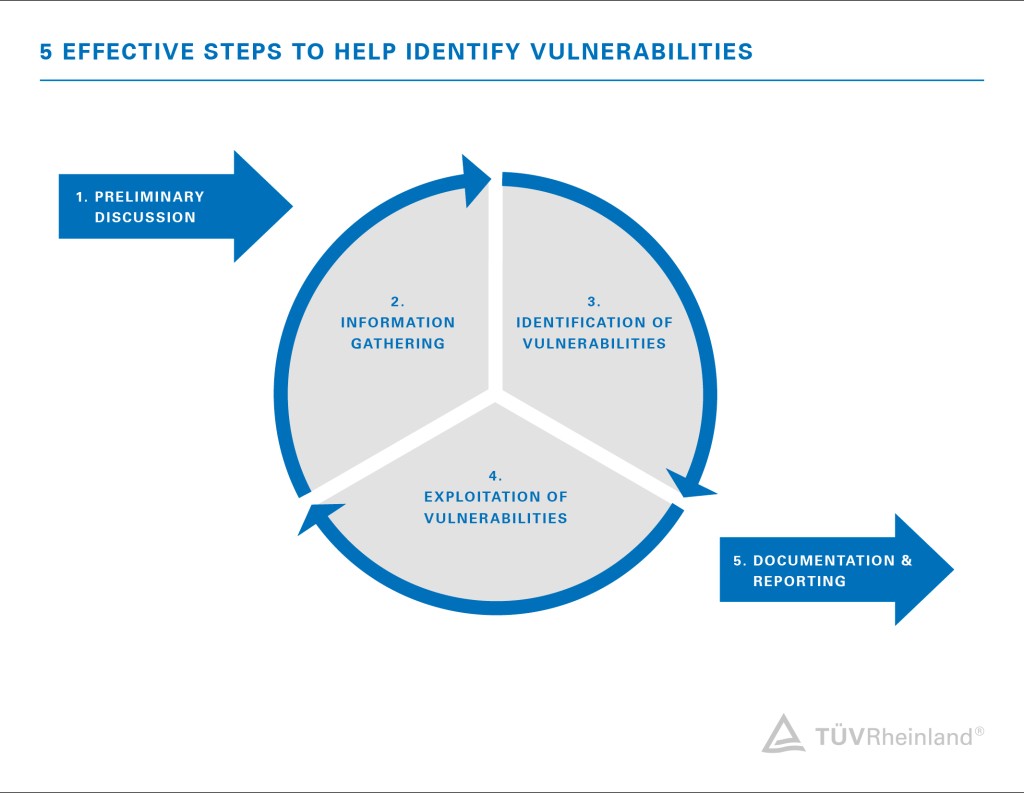
With the help of penetration testing, or pentesting, we check your existing IT infrastructure (networks and IT systems) and web applications (e.g. online shops, customer portals, online banking) and mobile applications for potential vulnerabilities that could provide criminals with a target for cyberattacks. In order to uncover vulnerabilities and security gaps and to optimally assess potential risks, our IT experts proceed as follows:
- Preliminary discussion and needs analysis:
Recording of the status quo to determine the goal and scope of the penetration test, according to your situation and risk profile. - Information gathering:
Gathering all information relevant to the attack and viewing the company from an attacker's perspective. - Identification of vulnerabilities:
Detection of potential vulnerabilities through targeted automatic and manual tests. In doing so, we apply similar methods that criminal hackers also use. - Exploitation of security vulnerabilities:
Detection of vulnerabilities by our testers deliberately exploiting security vulnerabilities and attempting to access protected company data, such as customer data. - Reporting
Summary of the penetration test results and all vulnerabilities found as well as recommendations for action to remedy them.
In the financial sector as well as in the automotive industry, penetration tests are already part of regulatory requirements. It is to be expected that other industries will follow because, regardless of the industry sector and the size of the company, sensitive data must be protected. We therefore recommend that you regularly check the security of your IT assets.
Trust our expertise in the field of penetration testing
Our penetration testing services are applicable to many areas of IT infrastructure. These include applications, networks and infrastructures, embedded systems, online stores, the intranet, IoT devices, and self-programmed software. Because we take a holistic view of IT security in your organization, we also offer testing that focuses on organizational, process, and human vulnerabilities rather than just technology. Tests with a focus that is not exclusively technical include phishing attacks, Red Team campaigns or technical security assessments.
The IT security of your company is what we care about. Therefore, with our cybersecurity testing services, we identify any kind of vulnerabilities and security vulnerabilities before others exploit them. In this way, we provide you with an objective overview of your deficiencies and subsequently support you with the appropriate recommendations for remediation. When it comes to cybersecurity audits, you can rely on our specialist and industry expertise, because testing is in our auditors' blood. We replace insecurity with security and help you protect your assets and the trust of your customers. TÜV Rheinland - tested with certainty.
Our Sustainability Initiatives
Nothing less than the future is at stake. Companies, institutions, public authorities and each and every one of us can play a positive role in shaping the path to tomorrow. We provide you with comprehensive support to ensure that you operate safely, sustainably and efficiently for many years to come.
Contact







/tuv-rheinland-business-continuity-management-bcm_core_4_3.jpg)

