These days, cloud-based applications are everywhere. We use them for work and in our private life without even realizing it. For example, we no longer want to do without Office 365, MS Teams, video streaming or social media because of the flexibility of these programs. Accessing company data from anywhere and collaborating on a global scale is almost impossible without the cloud. But what is practical for users poses major challenges for IT departments: How can the different cloud service models be integrated into the company’s existing IT? What about security when employees access sensitive data from many different devices? Who is liable in the event of data theft?
At TÜV Rheinland, we know the great potential of cloud solutions but also the challenges of cloud security. As an independent partner, we support you and help you achieve the maximum benefit from the cloud while ensuring maximum security, data protection and compliance.
Our Claim: Anytime, Anywhere, Any Connection – Always Secure!
Cloud Computing in Practice
IT managers and increasingly also non-IT departments are acquiring more and more software, platforms and infrastructure "as a service". Whether collaboration services, IoT platforms or CRM systems – there are cloud services available for any area of the digital value chain. As a result, companies are increasing their productivity and are driving the digital transformation. The 5G rollout will further accelerate cloud computing.
The following example shows the complexity and dynamic of cloud services use:
A company purchases resources from various providers, such as website hosting via Amazon Web Services. This solution simultaneously communicates with the CRM system that the company has installed on-premise. This, in turn, communicates with a data management system, which runs via Google Cloud. Since all these systems communicate with each other and exchange data, they all must be configured in a way that meets the company’s compliance and security policies at all times.
The 4 Key Benefits of Cloud Services
- Cost Efficiency: Cloud services dramatically reduce the cost of capital investment in IT infrastructure. Cloud services are billed based on the actual computing resources or storage volumes used; this so-called "pay-as-you-go" billing model scales the cost according to the depth of utilization.
- Business Transformation: Cloud services make it easier for companies to access new markets and services and to quickly change their own value chains. Companies can change their business and production processes in an agile manner and are less dependent on their company-maintained infrastructures and application environments, which sometimes can be sluggish.
- Business Agility: New performance features of cloud services are immediately available for application in operations. Therefore, businesses are less dependent on lengthy software rollouts. Other agility benefits include global availability, comprehensive analytics capabilities through AI or Big Data, and sophisticated security features.
- Mobility and Collaboration: Employees and business partners can access applications and data from anywhere, at any time, and on a wide range of devices, which enables interaction and collaboration.
Regardless of whether you use application software from the cloud (Software as a Service, SaaS), move your own IT infrastructure – entirely or partially – to the cloud (Infrastructure as a Service, IaaS), use application servers or interoperability services from the cloud (Platform as a Service, PaaS), or combine these three forms of operation – we at TÜV Rheinland are your competent partner for all levels of cloud computing and cloud computing security.
Cloud Strategy – The Framework for Comprehensive Cloud Security:
Conventional IT security is no longer sufficient for the digital transformation, which is characterized by more and more cloud services. The configuration of cloud security in different areas of application such as SaaS, IaaS and PaaS requires an integrated cloud security strategy. The cloud strategy forms the organizational framework for the systematic and sustainable implementation of cloud security. The cloud security strategy is always based on your corporate and IT strategy. Our experts will help you to develop a cloud security strategy that is specifically customized to your company, and will implement it together with you.
5 Core Principles That Illustrate Why a Cloud Security Strategy is Key for Your Business:
- It maintains agility, speed and flexibility.
- It ensures cost optimization.
- It upholds your company's data governance policies.
- It ensures compliance with relevant regulations such as the GDPR.
- It ensures efficient operation.
During the consultation, we answer key questions and assess risks. These questions may include:
- Which service models (SaaS – Software as a Service, PaaS – Platform as a Service or IaaS – Infrastructure as a Service) does your company use currently and will use in the future?
- Which providers does your company use?
- Are there dependencies on existing architectures or infrastructures?
- Does your company pursue a multi-cloud or a single-cloud approach?
- How are data protection requirements implemented currently and in the future?
Sustainably Secure with the Cloud Security Cycle
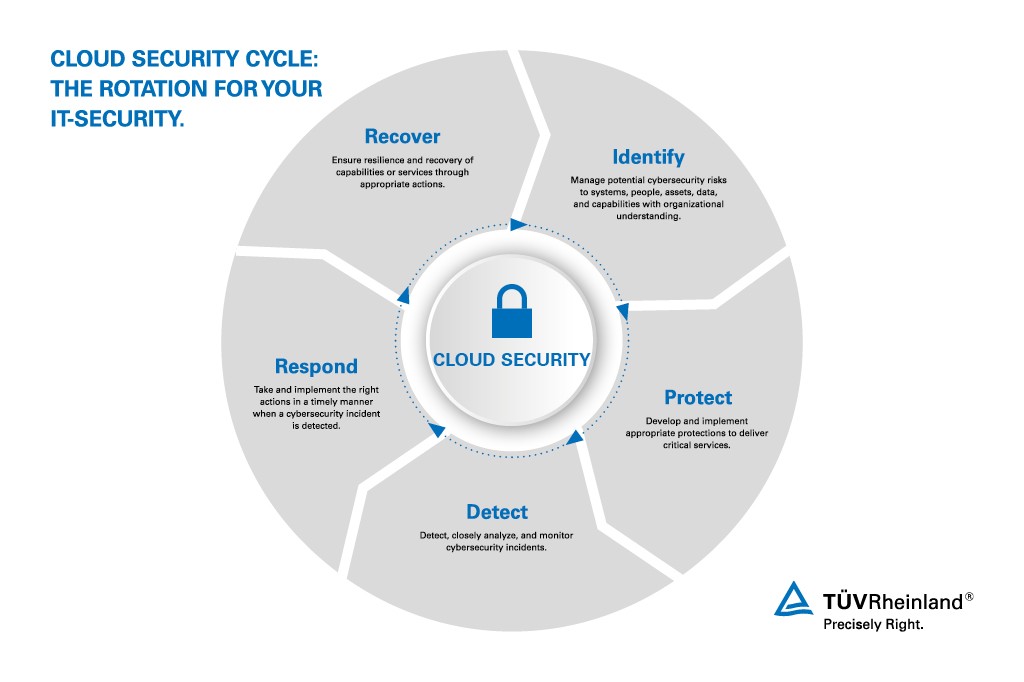
A cloud security strategy is not a one-time purchase or implementation, because the expectations for cloud services evolve too dynamically, and because there are new cloud providers and new services every day for you to choose from. Our comprehensive "Cloud Security Cycle" is your roadmap for continuously reviewing and optimizing your cloud security.
How the Cloud Security Cycle works
Each phase of the Cloud Security Cycle consists of individual measures and technical solutions that help you achieve the specific goal of that phase. The five phases are: Identify, Protect, Detect, Respond, and Recover. We advise you about the measures of each phase that are specifically helpful for your individual situation. If you complete all the phases of the Security Cycle, you will achieve a comprehensive cloud security.
Integrate cloud security into your business structure.
As your independent partner, we support you in developing and implementing a customized cloud security strategy. Our recognized IT specialists bring interdisciplinary expertise from the industry and the IT security environment to the table. Together we can protect your applications in the cloud in a comprehensive, proactive and sustainable manner.
With a customized cloud security strategy, your company can use cloud services securely without having to limit functions.


