Functional Safety and Cybersecurity Agility Life cycle process for security and safety
As companies undergo digital transformation within and with products and services, the threats to safety and security increases exponentially. Cyber-attacks, in particular, can be sensitively targeted for business disruption or manipulation.
Using advanced tools and processes, TRNA can assess and conduct tests to identify weaknesses and then design programs to ensure the business can constantly adapt to the changing threat profile, effectively achieving Cybersecurity Agility.
Cybersecurity Agility is the state where a business can rapidly adapt to changes with minimal business disruption
Cybersecurity Agility results in faster market launches, lower costs and safe and secure development of computing, storage, networking and cloud product and services. Therefore, it matters a lot to continuously assess risks comprehensively, prioritize them specifically, and implement solutions that protect your business based on risk. We know how to help you overcome the challenges.
Take a look at our comprehensive cybersecurity agility solutions.
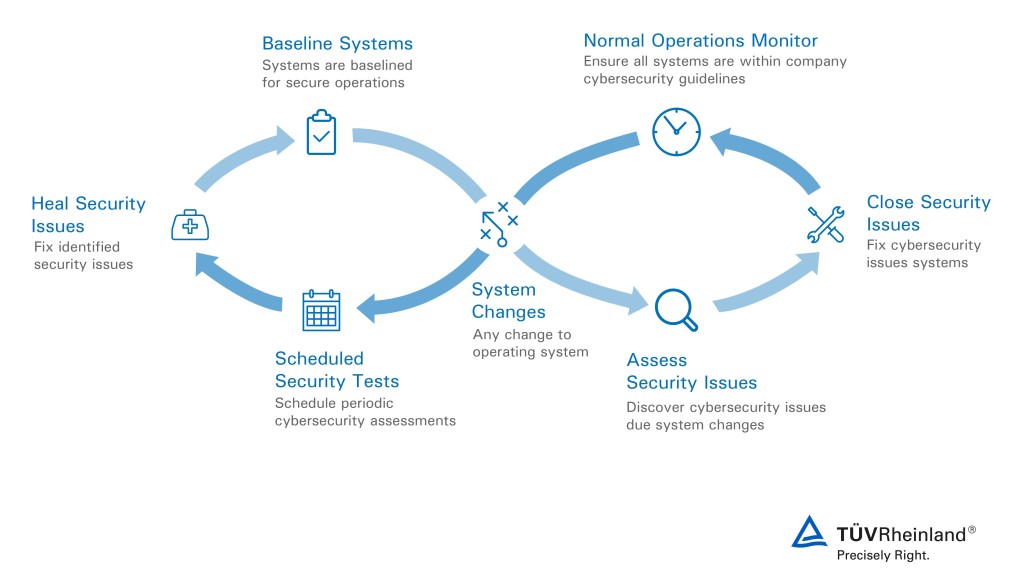
Cyber Agility Process to minimizing security risks
TRNA Cyber Agility Process is based upon internally developed tools, industry best practices, and standards such as NIST 800-115, ISO 27001/27002. Through the assessment and testing process, TRNA also integrates searches of Open-Source information for published Vulnerability Research on the target devices or applications.
Cybersecurity at TÜV Rheinland
For more than 20 years, the cybersecurity business at TÜV Rheinland has been helping companies from numerous industries to use innovative technologies securely with a global network of more than one hundred laboratories worldwide, in which all cybersecurity and data protection tests can be carried out for manufacturers from a single source.
Our consultants combine their cybersecurity expertise with a high level of industry know-how. The approach of our cybersecurity solutions aims to combine security and data protection in an increasingly vulnerable world of networked systems and devices.



-cybersecurity-services-1_core_4_3.jpg)
